Kitchen Pi
Sunday, April 6th, 2025

A project I did a while ago, the Kitchen Pi, was something I created to make cooking from a recipe easier. When not in use for recipes, the screen displays my outdoor cameras while idle. My kitchen cabinets have a hollow core, which I used to my advantage. I installed a 7” touchscreen LCD display and 3D-printed a bezel with heat-press inserts for secure mounting. I chose a Raspberry Pi 3B+ as the computer due to its minimal cooling requirements. However, this presented a challenge, as the 3B+ isn’t very powerful and modern web browsers are resource-intensive. I addressed this by focusing on three areas to improve efficiency.
While RISC OS is incredibly fast on the Raspberry Pi, it proved too buggy, and I encountered compatibility issues with many websites. I ultimately chose DietPi, a stripped-down version of Raspberry Pi OS. Even with DietPi, I still faced speed issues. Running the Chromium browser in kiosk mode helped by eliminating desktop overhead, allowing the Pi 3B+ to perform acceptably. Finally, I installed uBlock Origin Lite to remove ads—many of which not only clutter pages with junk but also autoplay videos and crash the browser. With these roadblocks addressed, I successfully tested the Kitchen Pi.
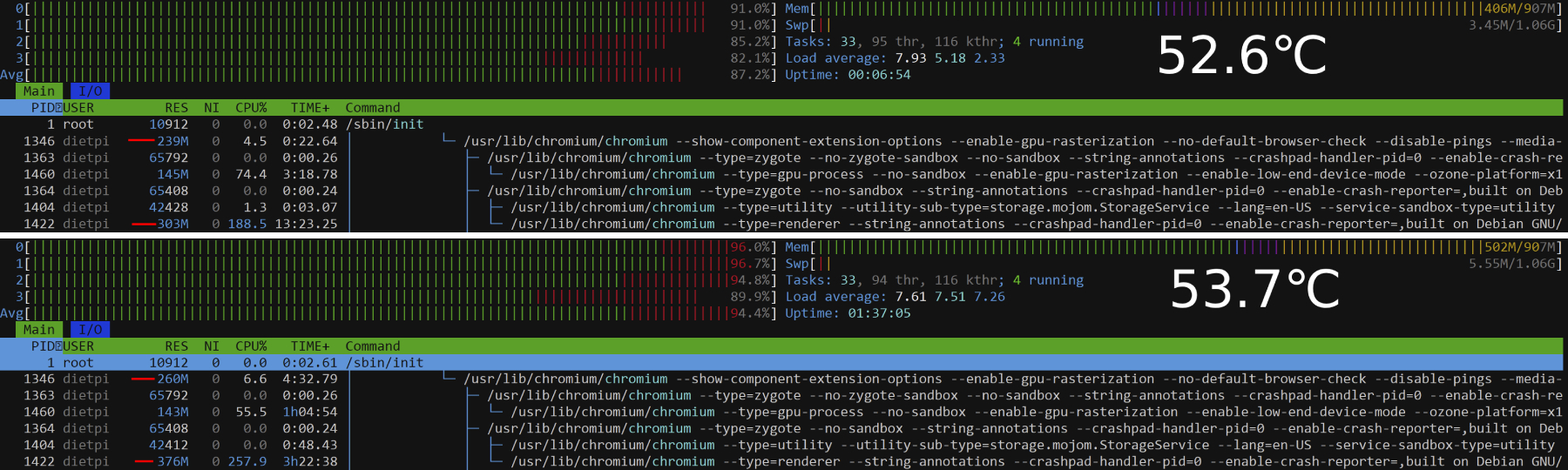
The final issue surfaced when I left the camera feed running overnight. After many hours of video streaming, the Raspberry Pi’s resources were completely exhausted, requiring a reboot. To investigate further, I ran a more comprehensive test by connecting via SSH and using the top command. Over time, it became clear that Chromium was slowly consuming all available RAM. Unable to find a better solution, I wrote a Bash script to parse /proc/meminfo and reboot the system if RAM usage exceeded 80%. That script is on https://github.com/BrendanClements/Tired-Resource A cron job was set to run every 30 minutes to execute the script. While not the most elegant fix, it works—and fortunately, I haven’t experienced the resource exhaustion issue since.
College Acceptance
Saturday, April 5th, 2025

Due to financial complications I withdrew from Champlain college where I was studying for a bachelor's degree in cybersecurity. The complications have been rectified, and I've once again been accepted. Classes start on May 5th.
CompTIA Security+ Certification
Friday, February 14th, 2025

Earning a CompTIA Security+ certification has been one of my goals. When I was first ready to take the exam, I discovered that the version I had studied for had been replaced with a newer one. I continued studying and successfully passed the updated exam on my first attempt. I am now Security+ certified and have begun preparing for the Network+ examination.
SSL Key Log File
Sunday, December 1st, 2024
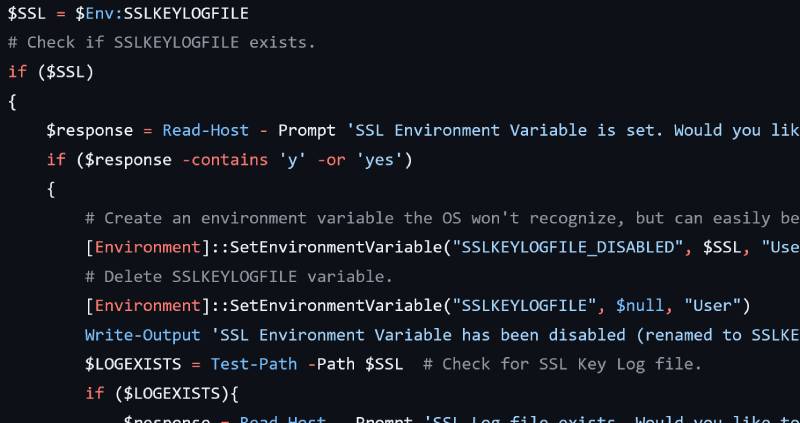
In the past, I've added an SSLKEYLOGFILE entry to my environment variables, which allows me to view web traffic data that is normally encrypted by TLS. This variable points to a file that accumulates the keys needed for decryption. However, leaving the environment variable activated means the file gradually fills with keys, making the data more vulnerable. It’s easy to forget about this setting after using it, so I wrote a PowerShell script designed to run at login to check if the variable exists and prompt the user for deletion.
By default, PowerShell does not have permission to modify environment variables. To address this, instead of changing permissions, I used a workaround by calling the PowerShell script from a batch script. I then utilized the Task Scheduler to execute the script at every logon. I uploaded the script to Github here.
Windows Event Viewer
Saturday, November 23rd, 2024
My recent use of the Windows Event Viewer made me realize that it is a tool I should regularly use, rather than waiting for issues to manifest. There are many different logs, and being familiar with how they appear during normal operation makes it much easier to identify anomalies when something goes wrong. To aid in this, I created two custom views within the Event Viewer.
The first view displays any event with ID 1102, which occurs when logs are cleared. Since I’ve never cleared any logs and don't plan to, the presence of this event would be an indicator of compromise (IoC), suggesting a malicious actor or program has compromised my computer, warranting further investigation.
The second view, named CEW, displays all log entries at the Critical, Error, or Warning levels. I now regularly use the CEW view to identify and address potential issues preemptively. Some issues have been more difficult than others to clear, but my constant attention to the errors will allow me to more easily track down future issues.
Network Diagnosis
Sunday, November 10th, 2024
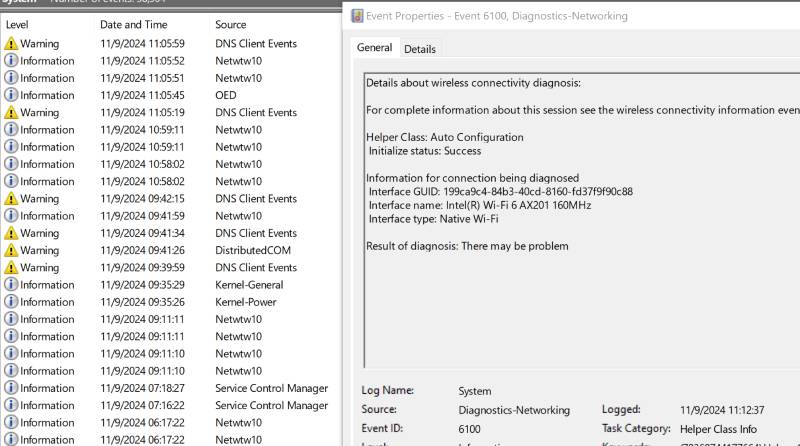
I was experiencing numerous network issues on my laptop. A SpeedOf.Me test revealed significantly reduced bandwidth, and at times the internet connection would drop out entirely. To diagnose the issue, I checked my desktop and cell phone, both of which appeared to work fine while connected to the same wireless network. I also tested my laptop on a different network, but the issues persisted. If the problem were in the physical layer of the OSI model, it would likely have been limited to the NIC or antenna in my laptop. I opened the Windows Event Viewer and found many network-related warnings, along with a surprising number of Netwtw10 informational entries. One entry was a "roam complete" log, and there were several warning lines caused by DNS failures.
Roaming is handled by layer two, while DNS operates on the application layer. With issues affecting multiple layers, I decided to first check the drivers. The Device Manager indicated that the best driver for the Intel(R) Wi-Fi 6 AX201 160MHz was already installed. I used to accept this at face value, but my research indicated that isn't always the case. I checked Intel's website and found an updated driver was available. Installing the updated driver resolved my networking issues and cleared up the numerous event log entries.
Had that not worked, I had a few troubleshooting steps in mind. First, I would have tried connecting via Ethernet. Then, I would have plugged in the Alfa WiFi adapter I normally use for wireless packet capture to see if the issue persisted. Lastly, I would have booted into Kali Linux to determine if the networking problems remained. The next steps would have depended on the success or failure of these tests.
Naming Plans & Planning Names
Tuesday, August 20th, 2024
I’ve been busy with many things, including studying for the CompTIA Security+ exam, which was updated to a new version without my knowledge after I had invested significant time studying for the 601 version. This unexpected development has limited the time I can devote to my Zant project. Admittedly, I’m not great at coming up with catchy names. Zant, derived from “cognizant,” constantly checks for local and global emergencies to provide early warnings for potential issues. It was originally called Doom, but I thought that name was too morose, so I renamed it to Zant.
The project was always intended to be one part of a larger vision. The other half will function more like a home assistant, monitoring local conditions, making adjustments to the home, communicating with Zant, and sending alerts when necessary. While brainstorming names, remembering that the project will consist of two parts, I landed on the perfect names: Cain and Abel.
After coming up with the names, I immediately recalled the Cain and Abel programs from the past, which were well-known in hacking and cybersecurity circles. Zant will be renamed Abel, while the home assistant will be named Cain. I’ve recently had a reason to start on Cain and get it minimally operational for surveillance purposes. When I leave home, I would like to be able to press a button to enable notifications for motion detected by my cameras instead of manually adjusting each setting. Monitoring home temperature to alert me if it drops in the winter, indicating a heater issue, will be my next focus. I have many plans but never enough time.
Email Security
Friday, August 9th, 2024
During the process of hardening my local infrastructure, I decided to set up an email address for my web domain. I configured the Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain Message Authentication, Reporting, and Conformance (DMARC) in keeping with best security practices. This was fortunate as my research quickly revealed that many email providers will automatically flag emails as spam if these protocols aren’t employed. I utilized Proton Mail to both enhance my security and simplify the configuration process. Proton Mail made the process incredibly simple, as all that was really required was for me to update the DNS records.
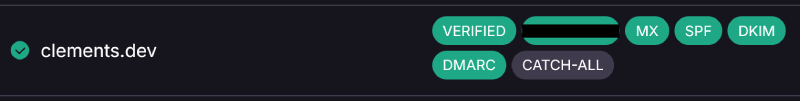 There is a TXT record that proves to Proton Mail that I own the domain, and another TXT record to enable SPF, designating who can send emails on behalf of that domain. This SPF record resolves to the authorized Proton IP addresses. DKIM uses asymmetric cryptography to sign the email, ensuring its integrity during transit. This is done by using a private key to sign the email content and embedding that signature in the header. The server receiving the email then uses a public key to verify the integrity of the message. Since the public and private keys are mathematically related, it is implausible for the content to match a signature created by the private key if it has been altered in any way. DMARC provides instructions to the recipient on how to handle emails that fail the SPF/DKIM check. I set mine to quarantine, as suggested by Proton Mail.
There is a TXT record that proves to Proton Mail that I own the domain, and another TXT record to enable SPF, designating who can send emails on behalf of that domain. This SPF record resolves to the authorized Proton IP addresses. DKIM uses asymmetric cryptography to sign the email, ensuring its integrity during transit. This is done by using a private key to sign the email content and embedding that signature in the header. The server receiving the email then uses a public key to verify the integrity of the message. Since the public and private keys are mathematically related, it is implausible for the content to match a signature created by the private key if it has been altered in any way. DMARC provides instructions to the recipient on how to handle emails that fail the SPF/DKIM check. I set mine to quarantine, as suggested by Proton Mail.
With my email now configured, I will update the contact page on my website. My main concern is the email being scraped, resulting in a lot of spam. If possible, I’d like to keep this particular inbox clear of irrelevant communication. I’ll upload this post and the updated contact information simultaneously. If you’d like to reach me, the information is in the contact link above, or you can click here.
Configuring SSH Public Key Infrastructure
Sunday, July 14th, 2024
 I've been taking steps to harden my infrastructure in terms of cybersecurity. There is always more that can be done to secure a network. I maintain good password hygiene, keep my systems up to date, and use high-quality networking equipment. My initial focus includes segmenting my network to isolate potentially risky devices, such as my DJI drone, disabling unnecessary services in both Windows and Linux, and setting up Public Key Infrastructure (PKI) for my SSH connections. I also use several Raspberry Pi devices for various projects. Today, my attention was on the one dedicated to my Zant project, which I had previously configured with SSH for local access.
I've been taking steps to harden my infrastructure in terms of cybersecurity. There is always more that can be done to secure a network. I maintain good password hygiene, keep my systems up to date, and use high-quality networking equipment. My initial focus includes segmenting my network to isolate potentially risky devices, such as my DJI drone, disabling unnecessary services in both Windows and Linux, and setting up Public Key Infrastructure (PKI) for my SSH connections. I also use several Raspberry Pi devices for various projects. Today, my attention was on the one dedicated to my Zant project, which I had previously configured with SSH for local access.
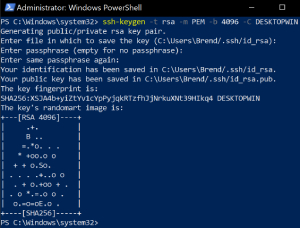
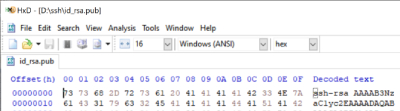 My goal was to set up asymmetrical encryption on the Raspberry Pi to authenticate access. Confidently, I began by taking screenshots to illustrate this process. Using PowerShell on my Windows laptop, I generated a public/private key pair. Interestingly, Windows identified the public key file, named id_rsa.pub, as a “Microsoft Publisher Document.” I opened the file using a hex editor and noticed that there wasn't a file signature in the header to identify the file type. While I've always known that the OS relies on the file extension, this made me wonder why there isn’t any comparison to the file signature.
My goal was to set up asymmetrical encryption on the Raspberry Pi to authenticate access. Confidently, I began by taking screenshots to illustrate this process. Using PowerShell on my Windows laptop, I generated a public/private key pair. Interestingly, Windows identified the public key file, named id_rsa.pub, as a “Microsoft Publisher Document.” I opened the file using a hex editor and noticed that there wasn't a file signature in the header to identify the file type. While I've always known that the OS relies on the file extension, this made me wonder why there isn’t any comparison to the file signature.
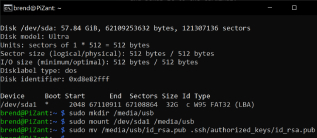 After generating the keys, I moved the private key to the .ssh folder on Windows. I then loaded the public key onto a flash drive and transferred it to the Raspberry Pi, which runs a Debian Linux distribution called Raspbian. I connected to the Pi, mounted the drive, and moved the public key into the .ssh/authorized_keys folder. Those familiar with Linux SSH keys will undoubtedly see my mistake. My first attempt failed, prompting me to change direction. Using PuTTYgen, I created a new key pair for use with WinSCP. After moving those keys to their respective locations, I attempted to connect again with WinSCP, but the server refused the key.
After generating the keys, I moved the private key to the .ssh folder on Windows. I then loaded the public key onto a flash drive and transferred it to the Raspberry Pi, which runs a Debian Linux distribution called Raspbian. I connected to the Pi, mounted the drive, and moved the public key into the .ssh/authorized_keys folder. Those familiar with Linux SSH keys will undoubtedly see my mistake. My first attempt failed, prompting me to change direction. Using PuTTYgen, I created a new key pair for use with WinSCP. After moving those keys to their respective locations, I attempted to connect again with WinSCP, but the server refused the key.
My research indicated that the refusal message likely meant an issue on the server side (my Raspberry Pi). This led me to realize my initial mistake: .ssh/authorized_keys is supposed to be a file, not a directory. If multiple keys are used, a config file needs to be created. I removed the directory and created an authorized_keys file, pasting the key into it. After this correction, I was able to authenticate with WinSCP using the certificate. To complete the process, I edited the /etc/ssh/sshd_config file to disable "PasswordAuthentication" by setting it to “no,” followed by executing “sudo systemctl restart ssh” in the terminal.
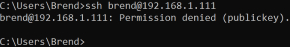 To test the setup, I tried to connect to the Raspberry Pi via the command line. However, the connection was immediately terminated with a "Permission denied (publickey)" message. This occurred because WinSCP uses a formatted version of the private key that isn’t compatible with the native OS. Knowing this, I plan to generate a new key pair and then copy/convert the private key to the format required for WinSCP so I can use both WinSCP and the command line. Subsequently, I will replicate the same procedure for my Kali Linux laptop and Windows desktop. This process will also be applied to my other Raspberry Pi devices and my Ubiquiti Cloud Key Gen2.
To test the setup, I tried to connect to the Raspberry Pi via the command line. However, the connection was immediately terminated with a "Permission denied (publickey)" message. This occurred because WinSCP uses a formatted version of the private key that isn’t compatible with the native OS. Knowing this, I plan to generate a new key pair and then copy/convert the private key to the format required for WinSCP so I can use both WinSCP and the command line. Subsequently, I will replicate the same procedure for my Kali Linux laptop and Windows desktop. This process will also be applied to my other Raspberry Pi devices and my Ubiquiti Cloud Key Gen2.
Supply Chain Vulnerabilties
Friday, June 28th, 2024
Supply chain attacks have become increasingly prevalent in the news, with some incredible saves thanks to astute individuals and, in some cases, sheer dumb luck. FireEye’s detection of malware implanted into SolarWinds thwarted what was arguably the most complex attack since StuxNet, but with a far more extensive attack surface. Malicious actors have found easier ways to gain access to their victims by infiltrating the supply chain, either by purchasing the rights to existing repositories or by taking over open source projects. Many of these incidents, fortunately, have been limited to money-making schemes, whereby malicious actors acquire established browser extensions or apps and flood them with unwanted ads for quick cash. However, the attack on the XZ Utils library, which is used by SSH in Debian, Fedora, Ubuntu Linux, and more, was different altogether.
Using social engineering, a malicious actor became a trusted developer and essentially took over the project. They established trust before cleverly hiding malicious code in compressed files used for testing, which inserted a backdoor allowing for remote code execution. With these high-profile supply chain attacks, the recent Polyfill.io attack reported by Sansec is particularly troubling (https://sansec.io/research/polyfill-supply-chain-attack).
Polyfill.io is a JavaScript library that helps with compatibility issues in older browsers. It was purchased by a Chinese company, which then modified the code to attack vulnerable devices using HTTP headers and IP location to selectively target victims, delaying the detection of the attack. This was possible because the JavaScript was hosted on the Polyfill.io website, allowing any changes to propagate immediately to the users visiting those sites.
I don’t typically use third-party JavaScript libraries like Polyfill or Bootstrap, as I haven't had the need for them. I strive to build websites with as little code as possible for search engine optimization and ease of use when writing and modifying them. However, given the numerous supply chain problems we've encountered (many of which are not mentioned here), it's crucial to know what code is being incorporated into our infrastructure. That said, I must admit I haven't been particularly scrutinizing when importing Python modules—something I intend to rectify.
Layer Three
Thursday, May 9th, 2024

While working on the Internet.py portion of my project, Zant, I was playing around with the ping method of the icmplib module. While verifying the packet transmission using Wireshark, I noted the payload was a seemingly random string of characters that changed with every request. To verify this behavior I followed the documentation which confirmed a random string would be generated if the payload parameter wasn’t specified. This means I can embed a message in the payload which I also verified with Wireshark. In my test displayed above I used a github link to the pertinent file which I may keep. It will be something to give network administrators context if they notice the persistent ICMP requests. How many admins monitor ICMP packets traveling through their network (when enabled)? It would be a great way for a malicious actor to smuggle information through a firewall.
Up and Running
Saturday, May 4th, 2024
Designing and coding a website after many years has been a profoundly educational experience. The once prevalent issues of cross-browser compatibility have largely been mitigated, mirroring the evolution of the World Wide Web. With its pervasive influence, the multitude of applications has necessitated the expansion of HTML and CSS standards, introducing an extensive array of tags, features, and properties.
Given that I do not intend to undertake further web design projects imminently, I am evaluating the extent of new skills I should acquire based on my immediate needs. While I may explore additional HTML and CSS functionalities in the future, I am currently adhering to the KISS (Keep It Simple, Stupid) philosophy. Also, determining the structure and naming of the pages posed quite a challenge.
The primary aim of this website is to share my expertise and thought process as I address different challenges, while also providing valuable insights on various topics. One particular focus is the SIM7600 GNSS HAT, and I will provide a link for further details once available. Instead of labeling this section as a "Blog," which implies an expectation of followers—a notion that does not align with my objectives—I have chosen "Thoughts" as a more fitting title for this section. The main sections of the website will be Home, Thoughts, Projects, and Contact.
Regarding the narrative style on the homepage, many websites feature third-person descriptions, which may be appropriate if the content were crafted by another person or a team. However, as this is my personal work and expression, I have decided to maintain a first-person narrative. If there are specific advantages to using third-person that I might be overlooking, I would welcome any insights.






 There is a TXT record that proves to Proton Mail that I own the domain, and another TXT record to enable SPF, designating who can send emails on behalf of that domain. This SPF record resolves to the authorized Proton IP addresses. DKIM uses asymmetric cryptography to sign the email, ensuring its integrity during transit. This is done by using a private key to sign the email content and embedding that signature in the header. The server receiving the email then uses a public key to verify the integrity of the message. Since the public and private keys are mathematically related, it is implausible for the content to match a signature created by the private key if it has been altered in any way. DMARC provides instructions to the recipient on how to handle emails that fail the SPF/DKIM check. I set mine to quarantine, as suggested by Proton Mail.
There is a TXT record that proves to Proton Mail that I own the domain, and another TXT record to enable SPF, designating who can send emails on behalf of that domain. This SPF record resolves to the authorized Proton IP addresses. DKIM uses asymmetric cryptography to sign the email, ensuring its integrity during transit. This is done by using a private key to sign the email content and embedding that signature in the header. The server receiving the email then uses a public key to verify the integrity of the message. Since the public and private keys are mathematically related, it is implausible for the content to match a signature created by the private key if it has been altered in any way. DMARC provides instructions to the recipient on how to handle emails that fail the SPF/DKIM check. I set mine to quarantine, as suggested by Proton Mail. I've been taking steps to harden my infrastructure in terms of cybersecurity. There is always more that can be done to secure a network. I maintain good password hygiene, keep my systems up to date, and use high-quality networking equipment. My initial focus includes segmenting my network to isolate potentially risky devices, such as my DJI drone, disabling unnecessary services in both Windows and Linux, and setting up Public Key Infrastructure (PKI) for my SSH connections. I also use several Raspberry Pi devices for various projects. Today, my attention was on the one dedicated to my Zant project, which I had previously configured with SSH for local access.
I've been taking steps to harden my infrastructure in terms of cybersecurity. There is always more that can be done to secure a network. I maintain good password hygiene, keep my systems up to date, and use high-quality networking equipment. My initial focus includes segmenting my network to isolate potentially risky devices, such as my DJI drone, disabling unnecessary services in both Windows and Linux, and setting up Public Key Infrastructure (PKI) for my SSH connections. I also use several Raspberry Pi devices for various projects. Today, my attention was on the one dedicated to my Zant project, which I had previously configured with SSH for local access. My goal was to set up asymmetrical encryption on the Raspberry Pi to authenticate access. Confidently, I began by taking screenshots to illustrate this process. Using PowerShell on my Windows laptop, I generated a public/private key pair. Interestingly, Windows identified the public key file, named id_rsa.pub, as a “Microsoft Publisher Document.” I opened the file using a hex editor and noticed that there wasn't a file signature in the header to identify the file type. While I've always known that the OS relies on the file extension, this made me wonder why there isn’t any comparison to the file signature.
My goal was to set up asymmetrical encryption on the Raspberry Pi to authenticate access. Confidently, I began by taking screenshots to illustrate this process. Using PowerShell on my Windows laptop, I generated a public/private key pair. Interestingly, Windows identified the public key file, named id_rsa.pub, as a “Microsoft Publisher Document.” I opened the file using a hex editor and noticed that there wasn't a file signature in the header to identify the file type. While I've always known that the OS relies on the file extension, this made me wonder why there isn’t any comparison to the file signature. After generating the keys, I moved the private key to the .ssh folder on Windows. I then loaded the public key onto a flash drive and transferred it to the Raspberry Pi, which runs a Debian Linux distribution called Raspbian. I connected to the Pi, mounted the drive, and moved the public key into the .ssh/authorized_keys folder. Those familiar with Linux SSH keys will undoubtedly see my mistake. My first attempt failed, prompting me to change direction. Using PuTTYgen, I created a new key pair for use with WinSCP. After moving those keys to their respective locations, I attempted to connect again with WinSCP, but the server refused the key.
After generating the keys, I moved the private key to the .ssh folder on Windows. I then loaded the public key onto a flash drive and transferred it to the Raspberry Pi, which runs a Debian Linux distribution called Raspbian. I connected to the Pi, mounted the drive, and moved the public key into the .ssh/authorized_keys folder. Those familiar with Linux SSH keys will undoubtedly see my mistake. My first attempt failed, prompting me to change direction. Using PuTTYgen, I created a new key pair for use with WinSCP. After moving those keys to their respective locations, I attempted to connect again with WinSCP, but the server refused the key. To test the setup, I tried to connect to the Raspberry Pi via the command line. However, the connection was immediately terminated with a "Permission denied (publickey)" message. This occurred because WinSCP uses a formatted version of the private key that isn’t compatible with the native OS. Knowing this, I plan to generate a new key pair and then copy/convert the private key to the format required for WinSCP so I can use both WinSCP and the command line. Subsequently, I will replicate the same procedure for my Kali Linux laptop and Windows desktop. This process will also be applied to my other Raspberry Pi devices and my Ubiquiti Cloud Key Gen2.
To test the setup, I tried to connect to the Raspberry Pi via the command line. However, the connection was immediately terminated with a "Permission denied (publickey)" message. This occurred because WinSCP uses a formatted version of the private key that isn’t compatible with the native OS. Knowing this, I plan to generate a new key pair and then copy/convert the private key to the format required for WinSCP so I can use both WinSCP and the command line. Subsequently, I will replicate the same procedure for my Kali Linux laptop and Windows desktop. This process will also be applied to my other Raspberry Pi devices and my Ubiquiti Cloud Key Gen2.